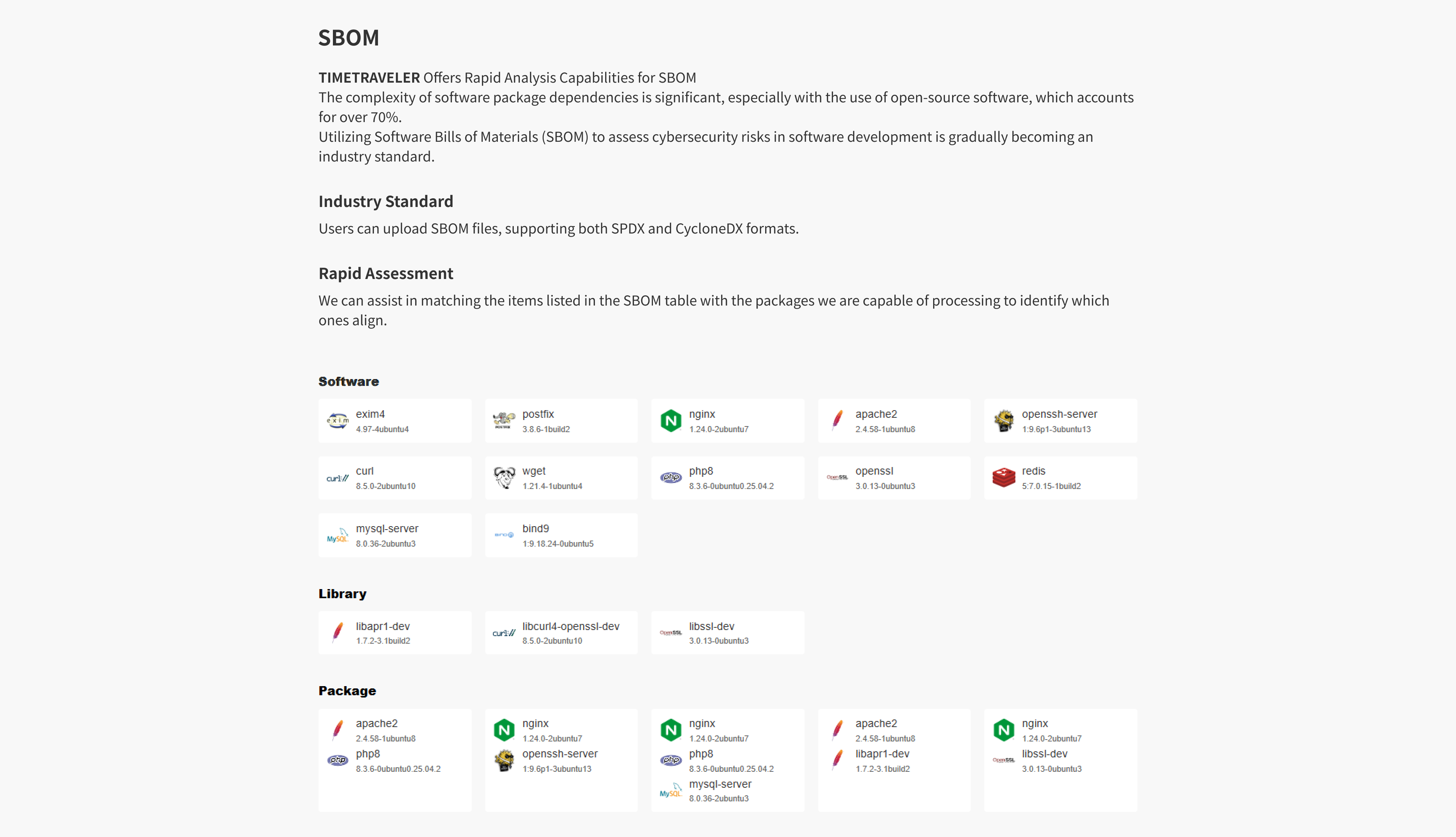
TIMETRAVELER utilizes #DAST-to-SAST technology to provide security rule pack for static analysis of applications, specifically targeting frameworks and third-party libraries.
False Negative
Most commercial static analysis software only operates at the level of programming language parsing. As a result, support for frameworks and third-party libraries is often incomplete.
This limitation affects both the call flow and data flow, leading to potential security vulnerabilities.
False Positive
Static analysis inherently lacks specific execution values and address information.
This leads to data flow paths that may appear correct, but the actual vulnerabilities are not exploitable.
Completing the Rule Packs
Through TIMETRAVELER's unique analytical capabilities, we can provide rule packs compatible with commercial software, specifically addressing unsupported packages.